Access Lists EcoRouter Documentation / Access Lists
- Policy-filter-list
- Prefix-list (prefix-list)
- No tags_en
- Filter-map
The EcoBNGOS supports various access lists. Access list is a set of text expressions-instructions which allows to "look inside" a frame/packet, match the text rule with a data inside a message and make decision of how to process this frame. The following access lists are supported in EcoBNGOS (short description below, read more in the relevant sections of this manual):
- Policy-filter-list;
- Filter-map;
- Prefix-list.
Policy-filter-list is used to filter route policies in various protocols of unicast and multicast routing, their promotion, redistribution, addition of special rules when processing routing information. Policy filter-lists CAN NOT be used for blocking or permit traffic to pass through the router.
Filter-map is used to block or permit traffic to pass through the router. It is also applicable in QoS, PBR and HTTP redirect scripts.
Prefix-list is similar to Policy-filter-list by functionality with the only difference, that allows the user to manage subnet masks more flexibly. These lists are widely used when configuring BRAS.
Policy-filter-list
The policy-filter-list is a feature which allows to create rule lists for filtering, redistributing, summarizing, and control of routing policies in different routing protocols.
The policy-filter-list is a variant of access list, where only the IP address and the inverse mask can be specified.
Filter lists are created in the configuration mode. There can be several rules in one filter list. The address of the network that is transmitted in the route update is indicated with a wildcard.
The syntax of rule creating and adding in policy-filter-list is: policy-filter-list <PFL_NAME> [deny | permit] <ADDRESS> <WILDCARD>.
Use the policy-filter-list <PFL_NAME> remark <DESCRIPTION> command to create description for policy-filter-list.
The policy-filter-list parameters are shown in the table below.
| Parameter | Description |
|---|---|
| PFL_NAME | Policy filter list number. The lists are numbered in the range from 1 to 99 and from 1300 to 1999 |
| permit | deny | Rule type: permit or deny |
| ADDRESS | Network IP address, specified as A.B.C.D. If the rule should be applied to all addresses, the parameter value must be any |
| WILDCARD | Wildcard mask, specified as A.B.C.D |
After creating the filter list, it must be applied to a specific routing process on the device.
The commands for adding filters differ depending on the protocol.
Command | Description |
|---|---|
Distribute-list <NUMBER> | Add filter list to OSPF routing context |
In | Apply incoming filter list |
Out | Apply outgoing filter list |
Basic configuration of filter list
ecorouter(config)#policy-filter-list 99 permit 172.168.1.0 0.0.0.255
where 99 is the name of the current filter list,
permit 172.168.1.0 0.0.0.255 is the argument indicating a routing update about this network is allowed.
After creating the filter list, it must be applied to a specific routing process on the device.
The commands for adding filters differ depending on the protocol.
Configuring Routing Information Filtering in BGP
The filter lists to be configured in the similar way as OSPF.
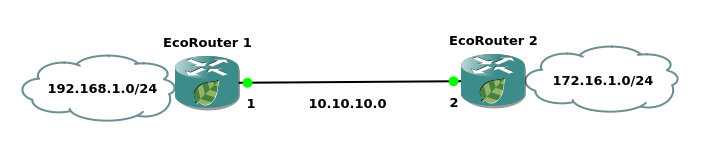
The use of the filter list differs.
To filter BGP route updates, the filter list is applied to a specific neighbor with a direction indicated.
Example of configuration
The filter list declining all the networks which start with 192 is created.
policy-filter-list 99 permit 192.0.0.0 0.255.255.255
The BGP routing process is configured, networks and neighbors are declared.
router bgp 100
network 10.1.1.0/24
network 10.2.0.0/16
network 172.64.1.0/24
network 172.64.2.0/24
network 172.64.3.0/24
network 192.1.1.0/24
network 192.1.2.0/24
network 192.2.3.0/24
network 192.128.1.0/30
network 192.129.1.0/30
neighbor 10.0.0.13
remote-as 200
The filter list is applied to the neighbor with the list number and the filtering direction.
neighbor 10.0.0.13 distribute-list 99 out
Thus the 10.0.0.13 neighbor will receive only the following networks in routing updates:
network 192.1.1.0/24
network 192.1.2.0/24
network 192.2.3.0/24
network 192.128.1.0/30
network 192.129.1.0/30
Configuring Routing Information Filtering in IS-IS
Between the routers 1, 2 and 3, dynamic routing is configured using the IS-IS protocol.
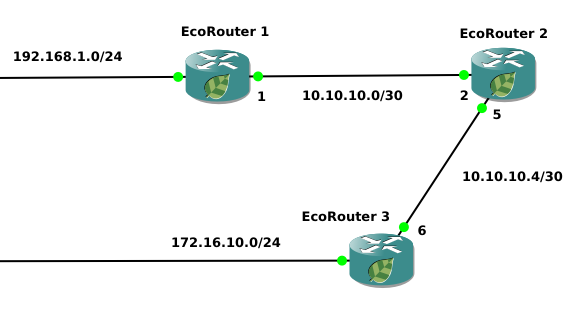
In the IS-IS protocol the filtering can be performed only during the redistribution process.
The current router configuration is shown below.
The router 1 operates on the level 1 as the router inside the zone.
EcoRouter_1#show run
router isis 1
is-type level-1
net 49.0001.0000.0000.0001.00
!
interface e2
ip mtu 1500
ip address 192.168.1.1/24
ip router isis 1
!
interface e1
ip mtu 1500
ip address 10.10.10.1/30
ip router isis 1
!
!
port te0
mtu 9728
service-instance 1
encapsulation untagged
no rewrite
connect ip interface e1
The router 2 operates on the levels 1 and 2.
EcoRouter_2#show run
router isis 1
net 49.0001.0000.0000.0002.00
!
interface e2
ip mtu 1500
ip address 10.10.10.5/30
ip router isis 1
!
interface e1
ip mtu 1500
ip address 10.10.10.2/30
ip router isis 1
!
port te0
mtu 9728
service-instance 1
encapsulation untagged
no rewrite
connect ip interface e1
!
port te1
mtu 9728
service-instance 1
encapsulation untagged
no rewrite
connect ip interface e2
The router 3 operates only on the level 2.
EcoRouter_3#show run
router isis 1
is-type level-2-only
net 49.0001.0000.0000.0003.00
!
interface e2
ip mtu 1500
ip address 172.16.10.1/24
ip router isis 1
!
interface e1
ip mtu 1500
ip address 10.10.10.6/30
ip router isis 1
!
port te0
mtu 9728
service-instance 1
encapsulation untagged
no rewrite
connect ip interface e1
Output of routing tables for topology.
EcoRouter_1#sh ip route Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
IP Route Table for VRF "default"
C 10.10.10.0/30 is directly connected, e1
i L1 10.10.10.4/30 [115/20] via 10.10.10.2, e1, 00:00:21
C 192.168.1.0/24 is directly connected, e2
EcoRouter_2#sh ip route
Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
IP Route Table for VRF "default"
C 10.10.10.0/30 is directly connected, e1
C 10.10.10.4/30 is directly connected, e2
i L2 172.16.10.0/24 [115/20] via 10.10.10.6, e2, 00:00:02
i L1 192.168.1.0/24 [115/20] via 10.10.10.1, e1, 00:00:03
EcoRouter_3#sh ip route Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
IP Route Table for VRF "default"
i L2 10.10.10.0/30 [115/20] via 10.10.10.5, e1, 00:00:09
C 10.10.10.4/30 is directly connected, e1
C 172.16.10.0/24 is directly connected, e2
i L2 192.168.1.0/24 [115/30] via 10.10.10.5, e1, 00:00:09
Creating the filter list to restrict routing updates about the network 192.168.1.0/24 from EcoRouter_1 to EcoRouter_3.
EcoRouter_3(config)#policy-filter-list 20 deny 192.168.1.0 0.0.0.255
where 20 is the filter list number,
deny is the denying argument,
192.168.1.0 0.0.0.255 is the network with the restricted routing updates.
After this, the list of filters should be placed in the router's routing context.
EcoRouter_2(config)#router isis 1
EcoRouter_2(config-router)#redistribute isis level-1 into level-2 distribute-list 20
where redistribute is the command to redistribute routes,
isis level-1 into level-2 is the argument indicating the route is taken inside the zone and is announced outside,
distribute-list 20 is the argument indicating the created filter list with a name.
This command will result the abscence of information about this network on EcoRouter 3.
EcoRouter_3#sh ip route
Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
IP Route Table for VRF "default"
i L2 10.10.10.0/30 [115/20] via 10.10.10.5, e1, 01:35:24
C 10.10.10.4/30 is directly connected, e1
C 172.16.10.0/24 is directly connected, e2
Configuring Routing Information Filtering in OSPF
Between the routers 1 and 2 dynamic routing is configured using the OSPF protocol.

| EcoRouter 1 | EcoRouter 2 |
|---|---|
EcoRouter_1#show run ! interface e2 port te0 | EcoRouter_2#show run router ospf 1 |
Output of the routing table on the EcoRouter_1 and EcoRouter_2.
| EcoRouter 1 | EcoRouter 2 |
|---|---|
EcoRouter_1#show ip route | EcoRouter_2#sh ip route Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default IP Route Table for VRF "default" C 10.10.10.0/24 is directly connected, e1 C 172.168.1.0/24 is directly connected, e2 O 192.168.1.0/24 [110/20] via 10.10.10.1, e1, 00:18:47 Gateway of last resort is not set |
Configure the filtering of the announcement of routing information from Ecorouter 2 on the Ecorouter router 1.
EcoRouter_1(config)#policy-filter-list 10 remark FilterForER2
Create a filter list numbered 10. Add a comment for this filter list.
EcoRouter_1(config)#policy-filter-list 10 deny 172.168.1.0 0.0.0.255
Create a rule in the filter list which restrict the route from being placed into the 172.168.1.0/24 network with the routing table.
Once created, the filter list must be applied to the routing process. Before applying the filter will not work.
EcoRouter_1(config)#router ospf 1
EcoRouter_1(config-router)#distribute-list 10 in
In the context of the routing protocol configuration, specify the filter list number and the filtering direction.
For OSPF, the use of filter lists is possible only on the incoming direction, because LSAs are not filtered in this direction, but only routes that are placed in the routing table.
EcoRouter_1#sh ip route
Codes: K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
IP Route Table for VRF "default"
C 10.10.10.0/24 is directly connected, e1
C 192.168.1.0/24 is directly connected, e2
Gateway of last resort is not set
There is no such network in the routing table.
EcoRouter_1#sh ip ospf database
OSPF Router with ID (192.168.1.1) (Process ID 1 VRF default)
Router Link States (Area 0.0.0.0)
Link ID ADV Router Age Seq# CkSum Link count
172.168.1.1 172.168.1.1 1552 0x80000007 0x8c39 2
192.168.1.1 192.168.1.1 1556 0x80000006 0x4447 2
Net Link States (Area 0.0.0.0)
Link ID ADV Router Age Seq# CkSum
10.10.10.1 192.168.1.1 1556 0x80000001 0x1fcd
EcoRouter_1#
Information about this network is present in the OSPF channel state database.
Prefix-list (prefix-list)
A prefix-list is an alternative ro policy-filter lists used in many filtration commands and have a number of advantages. Prefix-lists load a CPU less what increases a router performance.
Prefix lists show commands
The show ip prefix-list <name> and show ip prefix-list summary commands display general prefix-list information. The show ip prefix-list detail <name> command displays statistics on prefix-list matching (hit count) and on application matching (route-map) where a prefix-list is used (refcount).
| Command | Description |
|---|---|
| show ip prefix-list <name> | Displays specific prefix-list |
| show ip prefix-list summary | Displays all prefix-lists |
| show ip prefix-list detail <name> | Displays statistics on prefix-list matching (hit count), on application matching (route-map) where a prefix-list is used (refcount) |
Prefix Lists Configuration
Prefix-lists are checked in order row by row until matching to any clause is found. Just after the matching is found a packet processing starts. By default all packets not allowed directly in the prefix-list, are denied (an implicit operator deny all for all packets having no matches).
Use the ip prefix-list command to create prefix-list. The prefix-list name must be specified after. The command supports statement enumerating what the key word seq with a number after is used for. The statement can have any number from range <1-4294967295> (the smaller is a number the earlier a statement will be checked for matching). If the first statement has a number 10 and the last one has 15 the statements with a 11, 12, 13, 14 numbers can be added into the prefix-list at any time. If in the new prefix-list the first statement's number is not specifyed manually it will be assigned automatically to 5. The following statements will be enumerated automatically with a step equal 5. To disable the auto-enumerating mode use the no ip prefix-list sequence-number command. To define the subnet which information should be transmitted about to other routers use the permit key word, to restrict use the deny key word. The whole command is following:
ip prefix-list <prefix-list-name> seq <sequense-number> (permit | deny) <subnet/mask> (ge | le | eq <value>).
Use the ip prefix-list <prefix-list-name> description <text> command to specify description (up to 80 symbols).
In addition to direct specifying a subnet and a mask, prefix-list allows to select subnets by specifying the mask's length in operators ge, le, eq. Use the ge parameter to select specific prefixes which length is bigger than specified by <value>. Use the le parameter to select specific prefixes which length is smaller than specified by <value>. Use the eq parameter to select specific prefixes which length is equal to <value>. If all the ge, le, eq key word are omitted it means that an exact matching to the prefix-list statement is required. The following example explains on a 6 specified subnets:
1. 10.0.0.0/8
2. 10.128.0.0/9
3. 10.1.1.0/24
4. 10.1.2.0/24
5. 10.128.10.4/30
6. 10.128.10.8/30
Prefix-list matching
| Command | Subnets' IDs matching to a statemint |
|---|---|
ip prefix-list permit 10.0.0.0/8 | 1 |
ip prefix-list permit 10.128.0.0/9 | 2 |
ip prefix-list permit 10.0.0.0/8 ge 9 | 2,3,4,5,6 |
ip prefix-list permit 10.0.0.0/8 eq 24 | 3,4 |
ip prefix-list permit 10.0.0.0/8 le 28 | 1,2,3,4 |
ip prefix-list permit 0.0.0.0/0 | No match |
ip prefix-list permit 0.0.0.0/0 le 32 | All subnets. In this case instead of the 0.0.0.0/0 le 32 command it's possible to specify the any parameter when prefix-list configuring. |
The following command demonstrates an advertizing of subnets 10.0.0.0 with a masks from 10 to 20:
ip prefix-list TEST seq 5 permit 10.0.0.0/8 ge 10 le 20
ip prefix-list TEST seq 10 deny all
ATTENTION:
No tags_en
In the current version when using the prefix lists for BRAS configuration the ge, le, eq conditions are ignored.Use the no ip prefix-list <name> command to delete a specifyied prefix-list.
Filter-map
For L2 and L3 traffic filtering the filter-maps containig rules are used in EcoRouterOS.
The common logic when creating filter-map is following:
- Creating a filter-map by the filter-map {ethernet | ipv4} <FILTER_MAP_NAME> [<SEQUENCE_NUMBER>] expression.
- Specifiyng a rule by the match <CONDITION> expression, where <CONDITION> is a condition or conditions for packet examination (for more details, see the corresponding sections).
- Specifying an action by the set <ACTION> expression, where <ACTION> is the action that will be performed to packages that meet the criteria from <CONDITION> (for more details, see the corresponding sections).
Depending on protocols and conditions the rules can be specified differently.
For each filter-map, the rules are checked sequentially, in the order in which they appear in the show filter-map {ipv4 | ethernet} command's output.
If there are several traffic attributes in the rule, this is equivalent to logical operation "AND", that is, the rule will be applied only if the packet satisfies all the characteristics listed in the rule.
Example:
filter-map ipv4 example01 10
match tcp 10.0.0.0/24 eq 40 any eq 179 not-rst syn ack
set discard
This filtermap named example01 blocks TCP packets with source IP addresses (10.0.0.0-10.0.0.255) and port 40 to any destination IP address with port 179, which contains the SYN and ACK flags and does not contain RST flag.
To implement the logical operation "OR", several rules must be created. Then the rule will apply to the packet, the conditions of which the packet satisfies.
For example if any TCP packet which contains the SYN and ACK or packet which contains FIN should be allowed to pass the list must contain the following lines:
filter-map ipv4 example2 10
match tcp any any syn ack
match tcp any any fin
set accept
At the end of each access list there is an implicit rule that prohibits everything that is not allowed in this access list: any any discard.
Сonfiguring L2 filter-map
Another type of filter-map in EcoRouterOS is the filter-map ethernet, which allows to filter frames by the field value in the L2 header.
The filter-map ethernet differs by specific rule strucure: the source and destination MAC addresses, MAC wildcard masks and ethertype field values (optional) should be specified in the rule.
Filter-map ethernet is created in the configuration mode. Several rules can exist for one action.
The syntax for rule creating and adding into filter-map ethernet require to specify the following parameters:
- the name and the sequence value of имя filter-map ethernet - <FILTER_MAP_ETHERNET_LIST> [<SEQUENCE_NUMBER>];
- the rule - match {<SOURCE_MAC> <SRC_WILDCARD> | any | host <SOURCE_MAC>} {<DESTINATION_MAC> <DST_WILDCARD> | any | host <DESTINATION_MAC>} [<ETHERTYPE>];
- the action - set {accept | discard | port <PORTNAME>}.
The filter-map ethernet parameters are described in the table below.
| Parameter | Description |
|---|---|
| FILTER_MAP_ETHERNET_LIST | F ilter-map ethernet name, any value |
SEQUENCE_NUMBER | Execution priority number, value range - form 0 to 65535. If not specified the parameter will get the next available value with step 10 automatically |
| SOURCE_MAC | Source mac-address, should be specified in one of the three following formats:
If the rule should be applied to all addresses the parameter's value must be any. If the rule should be applied to the unic address the parameter's value must be host <MAC-address>. |
| SRC_WILDCARD | Source wildcard mask, should be specified in one of the three following formats:
|
| DESTINATION_MAC | Destination MAC address, should be specified in one of the three following formats:
If the rule should be applied to all addresses the parameter's value must be any . If the rule should be applied to the unic address the parameter's value must be host <MAC-address>. |
| DST_WILDCARD | Destination wildcard mask, should be specified in one of the three following formats:
|
| ETHERTYPE | Ethertype filed value. Значение поля ethertype. A hexadecimal value of the field can be specified in the range (0x600 - 0xffff) or in one of the following notations:
|
| set <ACTION> | |
| set accept | Allow the packet transit |
| set discard | Disallow the packet transit without sending ICMP notification |
| set reject | Disallow the packet transit with sending ICMP notification |
| set class-map <NAME> | The packets that fall under that rule are assigned the specified traffic class (class-map). The class must be pre-created (see "QoS configuration" for details) |
| set port <NAME> | Packets that fall under the rule are redirected to the specified port. NAME is the name of the port (see "Types of interfaces" for more information about ports) |
| set port <NAME> push <TAG> | Packets that fall under the rule are redirected to the specified port with the addition of a VLAN tag. Where NAME is the port name, TAG is the VLAN number |
| set port <NAME> pop <NUMBER> | Packets that fall under the rule are redirected to the specified port with the removal of VLAN tags. Where NAME is the port name, NUMBER is the number of tags that must be removed |
Each filter-map ethernet contain the last implicit prohibiting rule any any reject.
After the filter-map ethernet is created, rules are added, and action is specified it can be assigned to the service instance with a direction indication. In this case direction means the moment when packets passing through the interface will be processed by the filter-map ethernet: for filter-map ethernet only one direction is available, in - at the "input" to the interface. Multiple filter-map ethernet can be applied on one interface.
Use the set filter-map in <FILTER_MAP_ETHERNET_LIST> [<SEQUENCE>] command in the service instance context mode to assign the filter-map ethernet to service instance.
Example of filter-map ethernet configuration
The goal is to prohibit the arp-request from the client with address 0000.0000.000c.
ecorouter(config)#filter-map ethernet primer 10
ecorouter(filter-map-ethernet)#match host 0000.0000.000c any 0x806
ecorouter(filter-map-ethernet)#set discard
ecorouter(filter-map-ethernet)#ex
ecorouter(config)#filter-map ethernet primer 15
ecorouter(filter-map-ethernet)#match 0000.0000.0010 ffff.ffff.ff00 any
ecorouter(filter-map-ethernet)#set port ge0
ecorouter(filter-map-ethernet)#ex
ecorouter(config)#filter-map ethernet primer 20 ecorouter(filter-map-ethernet)#match any any
ecorouter(filter-map-ethernet)#set accept
ecorouter(filter-map-ethernet)#ex
The 0x806 value corresponds to the arp protocol. The "filter-map ethernet primer 20" allows all other traffic. Without this rule, the any any discard rule would be applied.
ecorouter(config)#port te0
ecorouter(config-port)#service-instance 1
ecorouter(config-service-instance)#set filter-map in primer 10
ecorouter(config-service-instance)#set filter-map in primer 15
ecorouter(config-service-instance)#set filter-map in primer 20
Сonfiguring L3 filter-map
Filter-maps are used to control the both-direction traffic through L3 interface. Direction in this case means the moment when the packets passing through the interface are processed by the filter-map: at the "input" of the interface - direction "in", at "exit" - the direction "out". Multiple filter-maps can be applied to the same interface in one direction. Each filter-map can be applied to several interfaces simultaneously.
There're two steps in filter-map use.
- Creating filter-map and adding rules into it.
- Binding filter-map to interface.
Filter-map can be created in configuration mode. Do the following steps to create filter-map (as a result the filter-map including one rule will be created):
- First line. Enter the filter-map ipv4 <FILTER_MAP_NAME> [<SEQUENCE_NUMBER>] command where <FILTER_MAP_NAME> is filter-map name, <SEQUENCE_NUMBER> is the. The parameters described in the table below.
- Second line. Specify the match <PROTOCOL> <SRC_ADDRESS> [<PORT_CONDITION>] <DST_ADDRESS> [<PORT_CONDITION>] [dscp <DSCPVALUE>] [<FLAG>] rule that the packets will be checked against. The parameters described in the table below.
- Third line. Specify an action that will be applied to packages that meet the conditions of the rule, by set <ACTION>. The parameters described in the table below.
Each filter-map can contain multiple rules. Follow the steps described above to add the rule into filter-map. Specify the <FILTER_MAP_NAME> of the filter-map where the rule should be added. The rule must have a unique <SEQUENCE> number within the same filter-map.
At the end of any filter-map ipv4 the implicite prohibiting rule any any reject is built in.
The common parameters of filter-map are described in the table below.
| Parameter | Description |
|---|---|
FILTER_MAP_NAME | Filter-map name, an arbitrary value |
SEQUENCE_NUMBER | Execution priority number, value range 0-65535. If the value is not specified, the parameter for the created filter-map ethernet will automatically receive the subsequent free value by step 10 |
| PROTOCOL | Protocol field value. Can be specified from range 0-255 or one of the shown below:
|
| SRC_ADDRESS | Source IP address, specified in one of the following formats:
|
| DST_ADDRESS | Destination IP address, specified in one of the following formats:
|
| DSCPVALUE | DSCP (Differentiated Services Code Point) value to check packet, integer from 0 to 63 |
| set <ACTION> | |
| set accept | Allow the packet transit |
| set discard | Disallow the packet transit without sending ICMP notification |
| set reject | Disallow the packet transit with sending ICMP notification |
| set nexthop <A.B.C.D> | Specify the next hop IP address. The packets that match the rule will be sent to the next hop, taking into account the routes in the RIB |
| set class-map <NAME> | The packets that fall under that rule are assigned the specified traffic class (class-map). The class must be pre-created (see "QoS configuration" for details) |
| set vrf <VRF_NAME> [<A.B.C.D>] | For the packets that match the rule, the vrf routing table will be used, where VRF_NAME is the name of the required vrf. For this vrf, you can specify the next hop IP address (optional) |
When specifying the udp protocol, the second line of the filter-map creation command will look like this: match udp <SRC_ADDRESS> [<PORT_CONDITION>] <DST_ADDRESS> [<PORT_CONDITION>] [dscp <DSCPVALUE>]..
The additional parameters related to the udp protocol are shown in the table below.
| Parameter | Description |
|---|---|
| PORT_CONDITION | Condition for the port value. One of the following values can be specified: {{eq | gt | lt} {tftp | bootp | <0-65535>} | range <0-65535> <0-65535>} |
| PORT_CONDITION values | |
| eq | Port number is equal to |
| gt | Port number is grearer than |
| lt | Port number is less than |
| tftp | UDP(69) |
| bootp | UDP(67) |
| <0-65535> | Exact port number, any value from the specified range |
| range <0-65535> <0-65535> | Port number is in range |
When specifying the tcp protocol, the second line of the filter-map creation command will look like this: match tcp <SRC_ADDRESS> [<PORT_CONDITION>] <DST_ADDRESS> [<PORT_CONDITION>] [dscp <DSCPVALUE>] [<FLAG>].
The additional parameters related to the tcp protocol are shown in the table below.
| Parameter | Description |
|---|---|
| PORT_CONDITION | Condition for the port value. One of the following values can be specified: {{eq | gt | lt} {ftp | ssh | telnet | www | <0-65535>} | range <0-65535> <0-65535>} |
| FLAG | The values of the flag by which packet processing can be distinguished. One of the following values can be specified (the not- prefix means that the specified flag is not set): urg | not-urg | ack | not-ack | psh | not-psh | rst | not-rst | syn | not-syn | fin | not-fin |
| PORT_CONDITION values | |
| eq | Port number is equal to |
| gt | Port number is grearer than |
| lt | Port number is less than |
| ftp | TCP(21) |
| ssh | TCP(22) |
| telnet | TCP(23) |
| www | TCP(HTTP-80) |
| <0-65535> | Exact port number, any value from the specified range |
| range <0-65535> <0-65535> | Port number is in range |
Example of filter-map creation and rule adding into it
The filter-map is created in configuration mode:
ecorouter(config)#filter-map ipv4 example 10
match udp 10.10.10.0/24 20.20.20.0/24 eq 22
set accept
Here:
- example – filter-map name,
- 10 - rule execution priority number in the filter-map,
- udp – protocol,
- 10.10.10.0/24 – source net where traffic is allowed from,
- 20.20.20.0/24 – destination net where traffic is allowed to,
- eq 22 – argument indicating the exact destination port number,
- accept – permitting argument (traffic that meets the conditions of the rule is allowed to pass through).
Adding a rule to this filter-map (for packets that match the rule, the accept action will also be executed, the rule will be applied the second in the filter-map named example). The rule adds a condition for verification. The action for the entire list is the same. The rules within the filter-map are checked in accordance with its <SEQUENCE> values.
ecorouter(config)#filter-map ipv4 example 20
match 1 host 192.168.1.15 host 172.20.100.1
Here:
- example – filter-map name,
- 20 - rule execution priority number in the filter-map,
- 1 – protocol, in this case ICMP,
- host 122.168.1.15 – exact source IP address where traffic is allowed from (the mask is not requiered here),
- host 172.20.100.1 – exact destination IP address where traffic is allowed to (the mask is not requiered here).
Adding a rule to this filter-map (for packets that match the rule, the accept action will also be executed, the rule will be applied the third in the filter-map named example).
ecorouter(config)#filter-map ipv4 example 30
match ospf 192.168.32.0 0.0.7.255 any
Здесь:
- example – filter-map name,
- 30 - rule execution priority number in the filter-map,
- ospf – the protocol name,
- 192.168.32.0 0.0.7.255 – source net specified by IP address and wildcard mask,
- any - destination network, all the IP addresses.
Displaing filter-map
Use the show filter-map ipv4 command to display existing L3 filter-maps. It displays only filter-maps without their interface bindings.
ecorouter#show filter-map ipv4
Filter map example
Filter 10
match udp 10.10.10.0/24 20.20.20.0/24 eq 22
match 1 host 192.168.1.15 host 172.20.100.1
match ospf 192.168.32.0 0.0.7.255 any
set accept
Filter map TEST
Filter 20
match any host 10.210.10.151 any
set accept
Use the set filter-map {in | out} <FILTER_MAP_NAME> [<SEQUENCE>] command in the context interface configuration mode to bind the filter-map to the specific interface. Multiple filter-maps can be bound to the one interface. In this case the <SEQUENCE> parameter is specified for each filter-map separately (not for the rules included!). All interface-bound filter-maps will be executed in order of increasing values of its <SEQUENCE>. The implicit "discard all" rule will be placed after the rules from all the bound filter-maps.
Example of filter-map binding to the interface
ecorouter(config)#interface e20
ecorouter(config-if)#set filter-map in example 10
ecorouter(config-if)#set filter-map out TEST 20
If the <SEQUENCE> value is not specified while binding the filter-list to the interface, then for each filter-map it is assigned automatically with an increment of 10.
The same filter-list can be assigned to multiple interfaces simultaneously.
Up to 64 thousand filter-maps can be created in EcoRouterOS. However, there is a limit for the number of "active" filter-map instances, that is, assigned to the L3 interface. A maximum of 64 assignements for filter-maps to interfaces can be configured. This restriction does not depend on the number of created filter-maps or interfaces.
Management of filter-maps can be carried out both from the main router, and from virtual routers. The filter-maps of the virtual router will be valid only within virtual router, and filter-maps of the main router, respectively, only within the main router.
Use the show counters interface <INTERFACE_NAME> filter-map {in | out} command to display filter-maps bound to the interface.
show counters interface e20 filter-map out
Interface e20
Filter map TEST
Filter 10 [0 packets]
match any host 10.210.10.151 any
set accept
Show L2 filter-map commands
Use the
show filter-map ethernet [<FILTER_NAME>]command in administration mode to display information about all existing L2 filter-maps where <FILTER_NAME> is the name of the filter-map.
Example:
Console | Description |
|---|---|
ecorouter#show filter-map ethernet | Display information about all the filter-maps |
Filter map FILTER Filter 10 match host 0000.0000.0001 host 0000.0000.0004 match host 0000.0000.0001 any 0x806 set accept Filter map test Filter 10 match host 0000.0000.0001 any 0x806 set discard | The information about all the filter-maps displayed |
ecorouter#show filter-map ethernet FILTER | Display information about the filter-map named FILTER |
Filter map FILTER Filter 10 match host 0000.0000.0001 host 0000.0000.0004 match host 0000.0000.0001 any 0x806 set accept | The information about the filter-map named FILTER displayed |
Show counters information
Use the
show counters port <NAME> filter-map {in | out} command in administration mode to display information about L2 filter-map counters.The command parameters are shown in the table below.
Parameter | Description |
|---|---|
<NAME> | Port name |
| in | out | Traffic direction |
The counters information displayed for each filter-map block and not for each rule.
Example:
Console | Description |
|---|---|
ecorouter#show counters port te0 filter-map in | Display filter-map counters information for port te0 incoming traffic |
Service instance 1 Filter map FILTER Filter 10 [5 packets] match host 0000.0000.0001 host 0000.0000.0004 match host 0000.0000.0001 any 0x806 set accept Filter 20 [6 packets] match host 0000.0000.0002 any set discard | The information for filter-map counters for port te0 incoming traffic displayed |
Use the show port <NAME> command in administration mode to display filter-maps binded to specific port where <NAME> is the port name.
Example:
| Console | Comment |
|---|---|
ecorouter#show port te0 | Display information for the port named te0 |
10 Gigabit Ethernet [none] port te0 is up MTU: 9728 LACP priority: 32767 Input packets 13, bytes 3308, errors 0 Output packets 10, bytes 1340, errors 0 Service instance te0.1 is up ingress encapsulation untagged ingress rewrite none egress encapsulation untagged egress none Connect bridge test symmetric filter-map in FILTER Input packets 13, bytes 3308 Output packets 10, bytes 1340 | Information displayed |
Show L3 filter-map commands
Use the show filter-map ipv4 command in administration mode to display all the L3 access lists.
ecorouter#show filter-map ipv4
Filter map NAME
Filter 10
match any any any
set discard
Filter map TEST
Filter 10
match any host 10.210.10.151 any
set accept
Use the show filter-map ipv4 <NAME> command to display the specific L3 access list.
ecorouter#show filter-map ipv4 TEST
Filter map TEST
Filter 10
match any host 10.210.10.151 any
set accept
Use the show counters interface <NAME> filter-map {in | out} command to display all the L3 access lists assigned to the specific interface.
ecorouter#show counters interface EXAMPLE filter-map in
Interface EXAMPLE
Filter map TEST
Filter 10 [0 packets]
match any any any
set discard
Policy configuration for subscriber session
The subscriber-policy is used to filter traffic in subscriber session. Up to 10 such policies can be set for one session. The traffic will be subsequently processed by each poliicy in accordance with its sequence number.
Use the subscriber-policy <NAME> command in configuration mode to create subscriber-policy where the <NAME> is the name of the entity created.
ecorouter(config)#subscriber-policy ?
SUBSCRIBER_POLICY Subscriber policy name
After the subscriber-policy is created its context configuration mode is automatically entered.
ecorouter(config)#subscriber-policy subspolname
ecorouter(config-sub-policy)#
The subscriber-poliicy parameters are shown in the table below.
Parameter | Description |
|---|---|
<BANDWIDTH> | Bandwidth in Mbit per sec, from 1 to 200 |
<DESCRIPTION> | Subscriber-policy description |
For each subscriber-policy 2 separate prosessing rules (filter-map policy) can be set: one for incoming (in) traffic) and one for outgoing (out) traffic. If no filter-map policy is set for direction the corresponding traffic will not be processed by this policy, and there will be no changes in this traffic. Attention: without specifying the limitations in filter-map policy and assignement it to the same direction for subscriber-policy the traffic will not be limited to the bandwidth specified.
Use the set filter-map {in | out} <NAME> command in subscriber-policy context configuration mode to set the filter-map policy to traffic direction where <NAME> is filter-map policy name.
The example of subscriber-policy configuration (in this example is assumed that the filter-map policy with the name FMPname is already created and configured; creating and configuring filter-map policy are described below).
ecorouter(config)#subscriber-policy subspolname
ecorouter(config-sub-policy)#description Testsubscrpolicy
ecorouter(config-sub-policy)#bandwidth in 200
ecorouter(config-sub-policy)#set filter-map in FMPname
Filter-map policy creating and configuring
Use the filter-map policy ipv4 <NAME> command in configuration mode to create filter-map policy where <NAME> is the filter-map policy name.
ecorouter(config)#filter-map policy ipv4 ?
FILTER_MAP_POLICY_IPV4 Filter map name
After the filter-map policy is created its context configuration mode is automatically entered.
ecorouter(config)#filter-map policy ipv4 FMPname
ecorouter(config-filter-map-policy-ipv4)#
Do the following steps to configure filter-map policy (as a result in the filter-map policy one rule will be created):
- First line. Enter the filter-map policy ipv4 <FILTER_MAP_NAME> [<SEQUENCE_NUMBER>] command where <FILTER_MAP_NAME> is filter-map name, <SEQUENCE_NUMBER> is the. The parameters described in the table below.
- Second line. Specify the match <PROTOCOL> <SRC_ADDRESS> [<PORT_CONDITION>] <DST_ADDRESS> [<PORT_CONDITION>] [dscp <DSCPVALUE>] [<FLAG>] rule that the packets will be checked against. The parameters described in the table below.
- Third line. Specify an action that will be applied to packages that meet the conditions of the rule, by set <ACTION>. The parameters described in the table below.
Each filter-map can contain multiple rules. Follow the steps described above to add the rule into filter-map. Specify the <FILTER_MAP_NAME> of the filter-map where the rule should be added. The rule must have a unique <SEQUENCE> number within the same filter-map policy.
The common parameters of filter-map policy are described in the table below.
| Parameter | Description |
|---|---|
| DIRECTION | Traffic direction, in - incoming traffic, out - outgoing traffic |
FILTER_MAP_NAME | Filter-map name, an arbitrary value |
SEQUENCE_NUMBER | Execution priority number, value range 0-65535. If the value is not specified, the parameter for the created filter-map ethernet will automatically receive the subsequent free value by step 10 |
| PROTOCOL | Protocol field value. Can be specified from range 0-255 or one of the shown below:
|
| SRC_ADDRESS | Source IP address, specified in one of the following formats:
|
| DST_ADDRESS | Destination IP address, specified in one of the following formats:
|
| DSCPVALUE | DSCP (Differentiated Services Code Point) value to check packet, integer from 0 to 63 |
| set <ACTION> | |
| set accept | Allow the packet transit |
| set discard | Disallow the packet transit without sending ICMP notification |
| set nexthop <A.B.C.D> | Specify the next hop IP address. The packets that match the rule will be sent to the next hop, taking into account the routes in the RIB |
| set redirect <REDIRECTNAME> | Redirect the HTTP GET to the specific <REDIRECTNAME>, where <REDIRECTNAME> is the name of the predefined URL (the redirection address must start with http://). An example of the redirection setting is shown below. |
| set reject | Disallow the packet transit with sending ICMP notification |
| set vrf <VRF_NAME> [<A.B.C.D>] | For the packets that match the rule, the vrf routing table will be used, where VRF_NAME is the name of the required vrf. For this vrf, you can specify the next hop IP address (optional) |
When specifying the udp protocol, the second line of the filter-map creation command will look like this: match udp <SRC_ADDRESS> [<PORT_CONDITION>] <DST_ADDRESS> [<PORT_CONDITION>] [dscp <DSCPVALUE>].
The additional parameters related to the udp protocol are shown in the table below.
| Parameter | Description |
|---|---|
| PORT_CONDITION | Condition for the port value. One of the following values can be specified: {{eq | gt | lt} {tftp | bootp | <0-65535>} | range <0-65535> <0-65535>} |
| PORT_CONDITION values | |
| eq | Port number is equal to |
| gt | Port number is grearer than |
| lt | Port number is less than |
| tftp | UDP(69) |
| bootp | UDP(67) |
| <0-65535> | Exact port number, any value from the specified range |
| range <0-65535> <0-65535> | Port number is in range |
When specifying the tcp protocol, the second line of the filter-map creation command will look like this: match tcp <SRC_ADDRESS> [<PORT_CONDITION>] <DST_ADDRESS> [<PORT_CONDITION>] [dscp <DSCPVALUE>] [<FLAG>].
The additional parameters related to the tcp protocol are shown in the table below.
| Parameter | Description |
|---|---|
| PORT_CONDITION | Condition for the port value. One of the following values can be specified: {{eq | gt | lt} {ftp | ssh | telnet | www | <0-65535>} | range <0-65535> <0-65535>} |
| FLAG | The values of the flag by which packet processing can be distinguished. One of the following values can be specified (the not- prefix means that the specified flag is not set): urg | not-urg | ack | not-ack | psh | not-psh | rst | not-rst | syn | not-syn | fin | not-fin |
| PORT_CONDITION values | |
| eq | Port number is equal to |
| gt | Port number is grearer than |
| lt | Port number is less than |
| ftp | TCP(21) |
| ssh | TCP(22) |
| telnet | TCP(23) |
| www | TCP(HTTP-80) |
| <0-65535> | Exact port number, any value from the specified range |
| range <0-65535> <0-65535> | Port number is in range |
Address for redirection specifying
ecorouter(config)#redirect-url SITEREDIRECT
ecorouter(config-redirect-url)#url http://forredirect.org
Example of configuration for traffic processing in subscriber session
In this example the static IPoE is configured.
As a result of the following settings, all incoming traffic of icmp type will be discarded at the input, incoming udp-traffic will be limited to 20 Mbps, incoming tcp-traffic will be skipped unchanged (by using filter-map policy named NAME1).
The outgoing traffic will be limited to 5 Mbps (by using filter-map policy named NAME2), outgoing tcp-traffic of port 80 will be redirected to the http://forredirect.org.
!
filter-map policy ipv4 NAME1 10
match icmp any any
set discard
filter-map policy ipv4 NAME1 20
match udp any any
set accept
filter-map policy ipv4 NAME2 10
match tcp any any eq 80
set redirect SITEREDIRECT
filter-map policy ipv4 NAME2 20
match any any any
set accept
!
subscriber-policy NAME
bandwith in 20
set filter-map in NAME1 10
bandwith out 5
set filter-map out NAME2 10
!
subscriber-service NAME
set policy NAME
!
ip prefix-list NAME seq 5 permit 10.10.10.100/32 eq 32
!
subscriber-map NAME 10
match static prefix-list NAME
set service NAME
!
interface ipoe.1
ip mtu 1500
ip address 10.10.10.1/24





