Pools and ACL EcoNAT Documentation / NAT configuration / Pools and ACL
- The concept of pools
- General settings
- Creating a pool
- Creating an ACL
- The procedure for determining the pool for the packet
- CGNAT pool
- Nat pool
- Static pool (1_to_1)
- Fake pool
The concept of pools
EcoNAT main configuration element are the so-called pools, characterized by a type of translations and a set of external (global) IPv4 address. Each pool is assigned its priority. The smaller the numerical value of the priority, the earlier the pool is processed. Each pool is associated with an ACL, which contains the selection criteria for a given pool depending on the content fields of the received IP packet.
Each pool can be either active (enable), or inactive (disable). Pool names always begin with the pool prefix.NOTE: You should not assign the same priority to several pools! This will lead that only the one pool, which was created first, will be used. The rest of the pools will be ignored.
General settings
In the system nat_defaults configuration branch there are common settings and system settings that are applied by default to all newly created pools (timeouts_inactivity and limits_peruser blocks are copied to the pool when it is created). Description of the parameters of this configuration branch is shown in the table below.
| Parametr | Description |
|---|---|
| vlan_mode | Processes/analyzes packets to a specified level of encapsulation. Possible parameter values: untagged, vlan, qinq |
| alg ftp | Enables ALG option for FTP protocol. Possible values: on/off |
| alg pptp | Enables ALG option for PPTP protocol. Possible values: on/off |
| alg rtsp | Enables ALG option for RTSP protocol. Possible values: on/off |
| alg sip | Enables ALG option for SIP protocol. Possible values: on/off |
| alg alg_on_bnat | Enables ALG option for static NAT. Possible values: on/off |
| sessions_per_translation | Number of active sessions per translation |
| udp_inbound_refresh | Enables updating the UDP translations with ingress (incoming) packets. Possible parameter values: on/off |
| l2mtu | The maximum size of MTU for incoming The value is specified for L2 with the L2-header. Default - 1522, maximum - 9692 |
| port_block_size | The size of port block. Default 128. It is strongly recommended not to change this value |
| portlimit_low | The value of used range "lower" ports (up to 1024-th) for each user. Possible parameter values: nolimit, 64, 128, 256, 512 |
| low_to_all_udp | Allows to use ports from the upper range if the ports from the lower range are exhausted. Possible parameter values: on/off |
| lldp | Enable (on) / disable (off) LLDP (on by default) |
| lldp_hostname "" | Hostname that will be used in LLDP advertisements |
| permit_invalid_flow | Enable (on) / disable (off) the function of establishing sessions on TCP segments for which the SYN flag is not set. The default value is off. A TCP session always starts with a segment with the SYN flag set, and such packets can be erroneous or malicious, therefore, by default, new sessions on such segments do not start, and the segments themselves are discarded. However, in some cases, this behavior can be useful, for example, in cases where part of the traffic goes along a different route or for the correct operation of TCP connections over which data is not transmitted for a long time. The functionality affects the behavior of the entire device and cannot be redefined in pools. To apply the changes, you must run the apply command |
| timeouts_inactivity {} | In this section is defined the inactivity time (in seconds) for different protocols and TCP states, after which an unused session will be closed forcibly |
| timeouts_inactivity translation | Sets the time in seconds before the expiry of which, even in the case of user inactivity, he will be guaranteed the allocation of ports of the same global IP. The recommended default value 86400 |
| timeouts_inactivity udp | Inactivity timeout in seconds for UDP sessions. The port on the global IP is released after this timeout. Default 300 |
| timeouts_inactivity icmp | Inactivity timeout in seconds for ICMP sessions. The port on the global IP is released after this timeout. Default 60 |
| timeouts_inactivity tcp_handshake | Timeout in seconds for a translation established by TCP packet with SYN flag set (unsteady TCP session). Default 4 |
| timeouts_inactivity tcp_active | Inactivity timeout in seconds for established TCP sessions in ESTABLISHED state. The port on the global IP is released after this timeout. Default 300 |
| timeouts_inactivity tcp_final | Inactivity timeout in seconds for TCP sessions. Default 240 |
| timeouts_inactivity tcp_reset | Timeout in seconds to reset TCP sessions. Default 4 |
| timeouts_inactivity tcp_session_active | Inactivity timeout in seconds for active TCP sessions. Default 120 |
| timeouts_inactivity udp_session | Inactivity timeout in seconds for active UDP sessions. Default 120 |
| timeouts_inactivity icmp_session | Inactivity timeout in seconds for active ICMP sessions. Default 120 |
| timeouts_inactivity other | Inactivity timeout in seconds for other IP-sessions (GRE for example). The protocol on the global IP is released after this timeout. Default 300. (applicable to NAT and 1:1 types of pools only) |
| timeouts_inactivity special | Inactivity timeout in seconds for protocols that require a larger timeout value. Default 600 |
| timeouts_inactivity special_tcp_ports ( ) | TCP ports to which to apply the increased timeout value |
| limits_peruser {} | Limit the number of ports to users |
| limits_peruser portlimit_icmp | This parameter describes the maximum number of simultaneously existing ICMP sessions for a user |
limits_peruser portlimit_tcp limits_peruser portlimit_udp | Limit the number of global (external) ports that can be assigned to one user (the local IP). It is recommended to set the values that are multiples of 64, from 64 to 32256. It makes sense to service providers to assign to ordinary users (individuals): from 1024 to 4096.Values less than 1024 may cause problems with the performance of some applications. Value greater than 32256 may result in that a user will be able to exhaust ports of IP addresses. For users, who are most demanding about the number of ports, it makes sense to create a separate CGNAT pool with a lower compression ratio (less local IP to one global), or use the NAT pool for allocation to a user of the whole IP with all the ports for the period of its activity |
Tcp_session_timeout, udp_session_timeout, icmp_session_timeout parameters triggered in the occasion when the translation is created and the first session appears. All other sessions will be created with the same parameters from timeouts_inactivity section (copied automatically from system nat_defaults).
Vlan_mode parameter may have the values: untagged, vlan, qinq. Where, untagged means that EcoNAT will process only untagged traffic, untagged and with one label – vlan, untagged, with one or two tags – qinq.
By default (untagged parameter value), EcoNAT passes transparently all traffic that are different from the standard IP, in order to smoothly transmit traffic on protocols such as BFD, OSPF, BGP, and so on. In particular, IP-packets with options (except for fragmented IP-packages with options), and also, tagged traffic are passed also without NAT.
If vlan mode is activated, EcoNAT will see label in the L2 header, look in to it and redirect the IP in accordance with the existing rules with the same label. Thus IP addresses under different labels should not overlap, because EcoNAT will see it as the same user. For example, if the packet comes with the IP address 192.168.1.100 and Tagged VLAN 100 and comes the packet with IP address 192.168.1.100 and Tagged VLAN 200, in fact it will be different users, but for EcoNAT, it will be the same address of the user. Therefore, the traffic may be disrupted.
To clear the translation table, use the clear sessions all command.
MyEcoNAT:1# clear sessions allSessions table purged
Translation table purged
Creating a pool
To create a pool, use the create pool <pool name> command. This creates a CGNAT pool with typical parameters (more about CGNAT pools, see paragraph 6.2.5) and named poolPOOL_NAME (prefixed «pool»). If the specified pool name already starts with the prefix «pool», eg, «pooltest», the name does not change, and in the future, this pool will be located in a pools configuration branch named pooltest. When you try to create a pool with an existing name, the pool will not be created. For example, if after changing the pooltest settings you try to create the pool named «test» (which will be automatically changed to «pooltest»), pooltest configuration will not be changed, and the new pool will not be created.
Then the values of pool parameters may be changed by going to the branch of a configuration tree corresponding to this pool (for details see the section Configurations).
EXAMPLE:
MyEcoNAT:1:# create pool test
MyEcoNAT:2:# goto pooltest
MyEcoNAT:3:pools.pooltest# show
type cgnat
enable
acl none
priority 100
global_ip ( )
port_range 1024:65535
hairpin on
connection_logging on
randomize_ports off
timeouts_inactivity
{translation 86400
udp 300
icmp 60
tcp_handshake 4
tcp_active 300
tcp_final 240
tcp_reset 4
tcp_session_active 120
udp_session 120
icmp_session 120
other 300
special 600
special_tcp_ports ( )
}
limits_peruser
{portlimit_icmp 1024
portlimit_tcp 1024
portlimit_udp 1024
}
As you can see in example, the ACL bindings is not performed when you are creating a new pool.
Pool parameters are described in the table below.
| Parameter | Description |
|---|---|
| type | Pool type: cgnat, static, nat, fake |
| enable или disable | Pool state |
| acl | ACL associated with the pool |
| priopity | Pool priority |
| global_ip ( ) | Global IP-addresses associated with the pool. To avoid ARP requests from the router to the EcoNAT WAN interface, it is not recommended to assign global_ip from the subnet of interfaces of routers between which EcoNAT is enabled |
| port_range | The range of external ports available for use on each global IP address owned by cgnat pool. The recommended value (range): 1024:65535. With these settings in each global IP will be available 64512 UDP and TCP ports as well |
| global_map ( ) | Consistency between global and local IP addresses. Addresses are set in pairs in the format <local address>[~vid] – <global address>. The parameter is valid for the static pool. The parameter is valid for pools of type static. Vid - VLAN identifier (from 0 to 4094). Optional parameter. The vid value is prefixed with "~" (tilde) without a space after the address |
| hairpin | Allows hairpinning. If the address on the external network coincides with the global address of one of the pools, EcoNAT will perform double translation without sending a packet outside (on the WAN). Hairpinning works only if it is allowed in both pools where users are connected in such a way |
| allow_external_connect | Allow external connection. The parameter is valid for the nat pool |
| connection_logging | Connection logging: (on) or (off) |
| randomize_ports | Allows port assignments from a block in a random order (on). Ports are allocated one-be-one if (off) |
| timeouts_inactivity | In this section is defined the inactivity time (in seconds) for different protocols and TCP states, after which an unused session will be closed forcibly. It is recommended not to change this parameters without purpose, one can use default settings instead |
| timeouts_inactivity translation | Sets the time in seconds before the expiry of which, even in the case of user inactivity, he will be guaranteed the allocation of ports of the same global IP. The recommended default value 86400 |
| timeouts_inactivity tcp_handshake | Timeout in seconds for a translation established by TCP packet with SYN flag set (unsteady TCP session). Default 4 |
| timeouts_inactivity tcp_active | Inactivity timeout in seconds for established TCP connections in the ESTABLISHED state. After this timeout port on the global IP is released. Default 300 |
| timeouts_inactivity tcp_final | Inactivity timeout in seconds for TCP sessions. Default 240 |
| timeouts_inactivity tcp_reset | Timeout in seconds to reset TCP sessions. Default 4 |
| timeouts_inactivity tcp_session_active | Inactivity timeout in seconds for active TCP sessions. Default 120 |
| timeouts_inactivity udp_session | Inactivity timeout in seconds for active UDP sessions. Default 120 |
| timeouts_inactivity icmp_session | Inactivity timeout in seconds for active ICMP sessions. Default 120 |
| timeouts_inactivity other | Inactivity timeout in seconds for other IP-sessions (GRE for example). The protocol on the global IP is released after this timeout. Default 300. (applicable to NAT and 1:1 types of pools only) |
| timeouts_inactivity special | Inactivity timeout in seconds for protocols that require a larger timeout value. Default 600 |
| timeouts_inactivity special_tcp_ports ( ) | TCP ports to which to apply the increased timeout value |
| limits_peruser | Limit the number of ports to users |
| limits_peruser portlimit_tcp limits_peruser portlimit_udp | Limit the number of global (external) ports that can be assigned to one user (the local IP). It is recommended to set the values that are multiples of 64, from 64 to 32256. It makes sense to service providers to assign to ordinary users (individuals): from 1024 to 4096. Values less than 1024 may cause problems with the performance of some applications. Value greater than 32256 may result in that a user will be able to exhaust ports of IP addresses. For users, who are most demanding about the number of ports, it makes sense to create a separate pool cgnat with a lower compression ratio (less local IP to one global), or use the nat pool for allocation to a user of the whole IP with all the ports for the period of its activity |
| limits_peruser portlimit_icmp | This parameter describes the maximum number of simultaneously existing ICMP sessions for a user |
These options are available depending on the pool type. The table below shows the parameters available for each type of pool.
| Parameters | cgnat | nat | static | fake |
|---|---|---|---|---|
| type | + | + | + | + |
| enable | + | + | + | + |
| acl | + | + | + | + |
| priority | + | + | + | + |
| global_ip ( ) | + | + | ||
| port_range | + | |||
| global_map ( ) | + | |||
| hairpin | + | + | + | + |
| allow_external_connect | + | + | ||
| connection_logging | + | + | + | + |
| randomize_ports | + | + | + | + |
| timeouts_inactivity | + | + | + | + |
| limits_peruser | + |
After the pool is created, it needs to add a global IPv4 address, this pool will use. To do this, enter the pool edit mode using the goto <pool name> or edit <pool name> command and type the global_ip add <global IP address> command. Type the global_ip remove <global IP address> command to remove the IP address in the pool edit mode.
MyEcoNAT:4:pools.pooltest# global_ip add 200.0.2.0/24
MyEcoNAT:5:pools.pooltest# show global_ip
global_ip ( 200.0.2.0/24 )
MyEcoNAT:6:pools.pooltest#
MyEcoNAT:4:pools.pooltest# global_ip
MyEcoNAT:5:(pools.pooltest.global_ip)# (
MyEcoNAT:6:(pools.pooltest.global_ip)# 10.11.22.1
MyEcoNAT:7:(pools.pooltest.global_ip)# 2.3.4.5
MyEcoNAT:8:(pools.pooltest.global_ip)# 188.165.1.1
MyEcoNAT:9:(pools.pooltest.global_ip)# )
MyEcoNAT:10:pools.pooltest# show
type cgnat
enable
acl none
priority 100
global_ip (
2.3.4.5
10.11.22.1
188.165.1.1
)
port_range 1024:65535
…
}
MyEcoNAT:11:pools.pooltest# global_ip -=(188.165.1.1 2.3.4.5)
MyEcoNAT:12:pools.pooltest# show
type cgnat
enable
acl none
priority 100
global_ip (
10.11.22.1
)
port_range 1024:65535
…
}
MyEcoNAT:13:pools.pooltest# global_ip +=(
MyEcoNAT:14:(pools.pooltest.global_ip)# 188.165.1.1
MyEcoNAT:15:(pools.pooltest.global_ip)# 111.1.1.255
MyEcoNAT:16:(pools.pooltest.global_ip)# 77.7.7.7
MyEcoNAT:17:(pools.pooltest.global_ip)# )
MyEcoNAT:18:pools.pooltest# show
type cgnat
enable
acl none
priority 100
global_ip (
10.11.22.1
77.7.7.7
111.1.1.255
188.165.1.1
)
port_range 1024:65535
…
}
MyEcoNAT:1:# analyze pooltest
# --- During processing pool 'pooltest' ----:
# No ACL associated with the pool
# use command 'use ACLNAME POOLNAME' to associate acl with a pool
MyEcoNAT:2:#
MyEcoNAT:1:# analyze pooltest
MyEcoNAT:2:#
MyEcoNAT:1:# edit pooltest
MyEcoNAT:2:pools.pooltest# disable
MyEcoNAT:1:# edit pooltest
MyEcoNAT:2:pools.pooltest# enable
Creating an ACL
After creating a pool, it is necessary to create an ACL determining which packets should be handled by that pool. Use the create acl <ACL name> command to create an ACL. This command creates an empty rule list called aclACL_NAME. Use the edit <ACL name> or goto <ACL name> command to open the rule list for editing.
The command for setting up a rule has the following syntax:
<num> <type> <protocol> <src>[~<vid>] <dst>
Optional parameters are enclosed in square brackets. Only values of the parameters are required in the command.
The table below describes all the parameters of the command.
Since the list of rules itself does not matter, it must be tied to a particular pool. The binding is done by applying use <ACL name> <pool name>.
EXAMPLE:
MyEcoNAT:1:# create acl a
MyEcoNAT:2:# goto acla
MyEcoNAT:3:acls.acla# show
acla {}
MyEcoNAT:4:acls.acla# 10 allow ip 194.85.16.0/24 any
MyEcoNAT:5:acls.acla# show
acla {10 permit ip src net 194.85.16.0/24 dst any
}
MyEcoNAT:6:acls.acla# use acla pooltest
MyEcoNAT:7:acls.acla# goto pooltest
MyEcoNAT:8:pools.pooltest# show
type cgnat
enable
acl acla
priority 100
global_ip ( )
…
Destination address is any by default.
MyEcoNAT:1:acls.acla# 10 allow ip 10.0.0.1
MyEcoNAT:2:acls.acla# show
acla {10 permit ip src host 10.0.0.1 dst any
}
MyEcoNAT:3:acls.acla#Source address is any by default, if you don’t specify other value, it is necessarily to use keyword dst in a command.
MyEcoNAT:1:acls.acla# 10 allow dst 40.0.0.1
MyEcoNAT:2:acls.acla# show
acla {10 permit ip src any dst host 40.0.0.1
}
MyEcoNAT:3:acls.acla#If you want to allow all possible addresses, the command will look like: 10 allow any any.
The procedure for determining the pool for the packet
When you receive a new IP packet (at the beginning of a new session), the pools are processed in the order of their priority: the priority value is smaller, the earlier this pool is processed. For example, if there are pools with the priorities of: 200, 150, 250, the first pool will be handled with priority 150.
Then will be analyzed the ACL, associated with a processed pool and the rules contained in the ACL are tested.
If the parameters of the received packet satisfy the allow rule, the packet will be processed by this pool. If the parameters of the received packet satisfy the conditions of a deny rule, then this pool will not be considered for this packet, and following pools will be considered in the priority order. If the packet does not satisfy the conditions of the current ACL rules, it examines the next rule of the pool or (if there are no rules anymore) moving on to the next pool in order of priority. If there are no more pools, the IPv4 packet will be transmitted without translation (like through the wire).
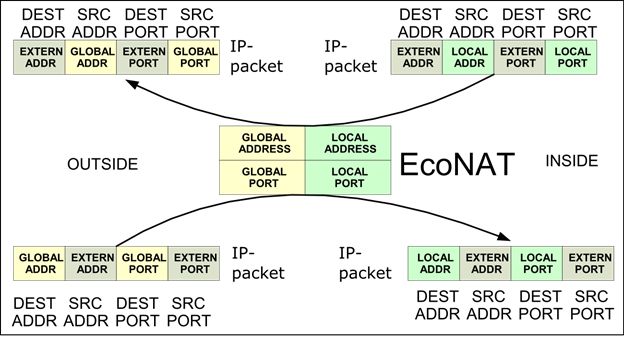
CGNAT pool
CGNAT pool provides Carrier-grade NAPT translation, in which the addresses and the ports are translated. Addresses and blocks of ports for client connections are allocated dynamically. Addresses allocation policy aims to equal ports filling of each global address. This gives the maximum benefit for the efficient use of IP addresses. Available parameters for this type of pools are represented in the table above in the section "Creating a pool".
Nat pool
Nat pool, otherwise referred to as the basic-NAT, provides only address translation (ports are not translated). Available parameters for this type of pools are represented in the section "Creating of a new pool".
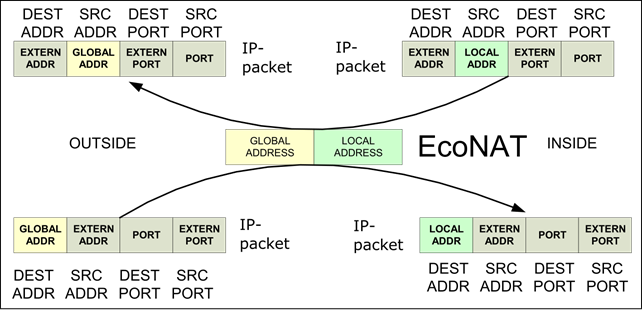
The cgnat pool type is generated by default when you are creating a pool, but you may change a pool type after its creating, assigning the corresponding value of the type parameter, located in the pool (nat for example).
Some of the parameters connected to cgnat pool disappears after changing its type to nat. Also, there a new option allow_external_connect appear, which allows outside connections. If you switch allow_external_connect to on, the translation may be established "by the initiative of" external hosts. This increases accessibility for peer-to-peer networks, as it will be able to connect from the outside at any ports to your users (unless, of course, the port is open on the host).
Usually, it makes sense to do two types of nat pool: one for those users who need connections initiated from outside (want to share torrents actively), and the other – for those customers who want to initiate connections only on their own initiative.
MyEcoNAT:1:# create pool b
MyEcoNAT:2:# goto poolb
MyEcoNAT:3:pools.poolb# type nat
MyEcoNAT:4:pools.poolb# show
type nat
enable
acl none
priority 200
global_ip ( )
hairpin on
allow_external_connect on
connection_logging on
randomize_ports off
timeouts_inactivity
{translation 86400
udp 300
icmp 60
tcp_handshake 4
tcp_active 300
tcp_final 240
tcp_reset 4
other 300
special 600
special_tcp_ports ( )
}
MyEcoNAT:5:pools.poolb#
Static pool (1_to_1)
Static pool – is a pool in which the address translation is set administratively. Available parameters for this type of pools are represented in the section "Creating of a new pool".
Each local address pool is uniquely mapped to a global address, port translation is not performed. Instead of a list of IPv4 global addresses that belong to a pool (instead of the global_ip parameter) there is a list of 1:1 translations (global_map parameter).
Translations in global_map parameter are defined as: <local address>[~vid] – <global address>. The parameter is valid for pools of type static. Vid - VLAN identifier (from 0 to 4094). Optional parameter. The vid value is prefixed with "~" (tilde) without a space after the address.
MyEcoNAT:1:# create pool c
MyEcoNAT:2:# goto poolc
MyEcoNAT:3:pools.poolc# type static
MyEcoNAT:4:pools.poolc# show
type static
enable
acl none
priority 100
global_map ( )
hairpin on
allow_external_connect on
connection_logging on
randomize_ports off
MyEcoNAT:5:pools.poolc# global_map += 192.168.0.5-200.0.0.3
MyEcoNAT:6:pools.poolc# global_map += (192.168.1.2~102-3.3.3.3)
MyEcoNAT:7:pools.poolc#
You may not specify the ACL for a static pool, in this case, it is implicitly assumed that the ammount of rules will be applied to the pool: allow ip src <local address> dst any.
If the ACL is still defined and configured, it is first checked, and then those which is implicitly assumed.
ATTENTION! If an ACL is attached to a static pool, then the list should not include the line permit any any.
Fake pool
Fake pool type intended for handling addresses that do not need translation (for example, if you need URL filtering, but do not need NAT translation for the addresses). The use of this type of pool is described in paragraph "Configuring URL Filtering for addresses that do not fall under the NAT". Available parameters for this type of pools are represented in the section "Creating of a pool".





