URL Filtering configuration EcoNAT Documentation / URL Filtering functionality (DPI) / URL Filtering configuration
The settings of the URL filtering functional (DPI) are stored in the system.dpi branch of the configuration tree. This branch contains general system settings for URL filtering and websites lists settings, which in the EcoSGE concept are called dpilistN, where N is a sequence number from 0 to 16.
EcoSGE:# go dpi
EcoSGE:system.dpi# ls
enable
functionality_mode normal_nat
revisors ( )
dpilist0
{
enable
rkn_source rkn
rkn_login "0123456789"
rkn_password "q1w2e3r4t5y6u7i8o9p0"
rkn_proxy ""
upload_dump_server ""
whitelist_mode off
log_matches off
log_pictures off
exceptions off
behaviour block
redirect_use_interval off
redirect_interval 600
redirect_interval_url 2592000
redirect_url "http://www.provider.ru/blocked/block0.html"
color_direction both
color_tos_byte 32
download_url "http://192.168.10.1/dump.xml"
update_schedule interval 600
protocols ( )
no_ip ( 10.210.0.123~0-4095 )
no_ip_remote ( )
ip (
10.0.0.0/8~1-10
61.216.14.0/23~0-4095
)
no_ipv6 ( )
ipv6 ( )
}
dpilist1
{
disable
whitelist_mode off
log_matches off
log_pictures off
exceptions off
behaviour block
redirect_use_interval off
redirect_interval 600
redirect_interval_url 2592000
redirect_url http://www.provider.ru/blocked/block1.html
color_direction both
color_tos_byte 32
download_url http://www.provider.ru/blacklists/list1.txt
update_schedule never
protocols ( )
no_ip ( )
no_ip_remote ( )
ip ( )
no_ipv6 ( )
ipv6 ( )
}…
To enable or disable URL filtering functionality use enable and disable contextual command of the system.dpi branch of the configuration tree.
In addition, each of the lists may be individually enabled/disabled with the enable and disable command, running in the configuration space of the list.
EcoSGE can operate in two modes:
- standard NAT, standing "in the gap" connection (the first figure below),
- and dual-mirroring traffic mode (the second figure below).
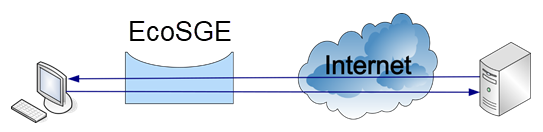
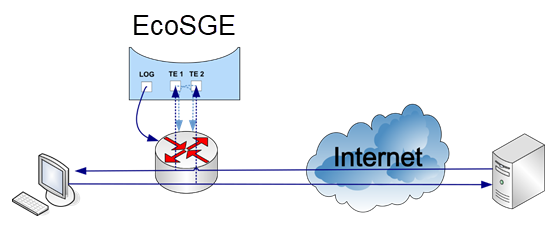
Modes of EcoSGE operation are switched with parameter functionality_mode, which may have values, respectively, normal_nat and double_mirrored_traffic. To switch between these modes you should run the command functionality_mode normal_nat or functionality_mode double_mirrored_traffic in the system.dpi configuration branch.
In mirroring mode EcoSGE listens to incoming and outgoing traffic, carrying out its translation, as in the normal mode. While outbound subscriber traffic is being mirrored on a local (even) EcoSGE interfaces, and the incoming from the Internet to subscribers – at the global (odd) EcoSGE interfaces (see more in "Interfaces" paragraph). If EcoSGE detects the connection with the prohibited resource, it sends through a router, the interrupting connection packet (for HTTPS) or redirecting packet (for HTTP). To send redirection or interrupting connection packet EcoSGE uses log interface or interfaces (see more in "Hardware" paragraph), while normally the same network interfaces to which subscribers are connected used for this. Therefore, for the correct operation of the mirroring scheme the default gateway address in the connection_log context must be configured in EcoSGE (see more in "Logging" paragraph). It is also recommended to take steps to prevent the duplicated traffic back to the network through the interface from which mirrored traffic is sent to the EcoSGE.
If traffic with a tag (or double tag) is mirrored to EcoSGE, in this case the redirect packets, and the interruption of the connection packets are encapsulated accordingly. Therefore, it is necessary to provide L2 connectivity EcoSGE logged interface and the router interface (IP-address specified as the default gateway in the connection_log context). In this case, you can configure EcoSGE in such a way that untagged traffic will be sent from the logging interface. To do this, you must configure the value on of the strip_tags parameter in the connection_log branch of the configuration tree.
Parameters for the lists of sites is in a table below.
| Parameter | Description |
|---|---|
enable or disable | Determines the activity of this list |
whitelist_mode | Determines whether the white or black list. Blacklist (parameter value - off) shows the sites which is denied for visiting. White list (parameter value - on) shows the sites which allowed for visiting (it is used for "children's Internet" for example). ATTENTION! If you use the whitelist, you can completely block access (see the explanation at the bottom of the table) |
log_matches | Specifies logging enabling of prohibited sites visiting on the server |
log_pictures | Determines whether the logging of images on the site is enabled. The following formats are considered: * .bmp, * .gif, * .jpeg, * .jpg, * .png, * .tif, * .tiff |
exceptions | Applies the list of exceptions to this dpilist. Possible values: on, off |
behaviour | Determines what action will be taken when the condition is met the given list (for black or not triggered for white list):
|
redirect_use_interval | Enables redirection timers. If you turn off this setting, redirection will be triggered every time you try to access any site from the list. Possible values: on, off |
redirect_interval | The interval between the redirection for the sites in the list (seconds). Default 10 minutes (600). After the first redirecting all other sites from the list will be opened within 10 min in the normal mode |
redirect_interval_url | The interval between the redirections of the same page. By default, 30 days (2592000). When you try to visit the page from the list the redirection is triggered. After that, this page will be opened in the normal mode for 30 days, then redirection will occur |
redirect_url | URL, where will be redirected the HTTP connection if the condition list triggered (for the black list) or didn't triggered (for the white list). EcoSGE is capable to add some client specificators to the address string. It helps to personalize the redirection site. Used specificators: %c - send to redirect_url the callback-id received from the RADIUS server; The redirect_url parameter format: <URL>/?<VAR_NAME1>=<SPEC1>&<VAR_NAME2>= <SPEC2>..<VAR_NAMEN>=<SPECN> where URL -redirection sites address, VAR_NAME1 .. VAR_NAMEN - variable name, SPEC1 .. SPECN - specificator. For example, http://example.com/?var1=%u&ip=%i&qwe=%v2. In this case if client will try to address to forbidden.com, it will be redirected to: http://example.com/?var1= forbidden.com&ip=10.1.1.10&qwe=0 |
color_direction | Marked direction of traffic:
|
color_tos_byte | The value that will be set in the type of service field in the packet header is specified in decimal format |
download_url | URL where the list will be uploaded in the case of auto-update (HTTP, FTP, TFTP protocols are supported). For dpilist0 - the address where will be preuploaded list |
update_schedule | Schedule, by which a list will be uploaded. Possible formats schedules: never – will never be uploaded, interval <SECONDS> – the number of seconds between auto-updates. It is recommended to put a value not less than 1 hour (3600 seconds). It is highly not recommended to set the value less than 5 minutes (300 seconds) |
protocols | A list of protocols to be blocked. To specify multiple protocols, use space as delimiter. |
no_ip | A list of IPv4 addresses that are excluded from the list of actions (no_ip parameter is processed earlier than the ip) |
| no_ip_remote | |
ip | A list of IPv4 addresses that appear to be under influence of the list |
no_ipv6 | A list of IPv6 addresses that are excluded from the list of actions (no_ipv6 parameter is processed earlier than the ipv6) |
ipv6 | A list of IPv6 addresses that appear to be under influence of the list. In order to specify the processing of all addresses, you must specify: ::/0 |
ATTENTION!
If you set the whitelist mode on parameter and add at least one IP address to the list (for example, 127.0.0.1), all IP addresses other than 127.0.0.1 will be blocked for clients specified in the dpilist configuration.
The whitelist can contain only IP addresses, only URLs or IP addresses and URLs.
If there are IP addresses and URLs in the list, then for each URL there must be a corresponding IP-address (addresses) to which it will be converted.
If there are only URLs in dpilist, you do not need to assign IP addresses.
If the address falls within the range specified in the value of the ipv6 parameter, the corresponding subscriber sessions are created. The status of these sessions can be checked using the show sessions local any command.
EcoSGE:system.dpi# show sessions local any
ipv6 egress UDP [2001:DB8:3333:4::5]:58712-[2001:DB8:3333:4::10]:33435; Last packet 6.10 seconds ago; To be deleted in 293.90 seconds of inactivity.
ipv6 ingress UDP [2001:DB8:3333:4::5]:33435-[2001:DB8:3333:4::10]:63607; Last packet 37.46 seconds ago; To be deleted in 262.54 seconds of inactivity.
For IPv6 diagnostics, a number of counters are used, as shown in the table below.
| Counter | Description |
|---|---|
cr_ipv6_table_entries | Number of entries in the IPv6 session table |
cr_ipv6_established_sessions | Total number of IPv6 sessions installed |
cr_ipv6_egress_packets | Number of IPv6 packets in the egress direction |
cr_ipv6_ingress_packets | Number of IPv6 packets in the ingress direction |
cr_ipv6_egress_bytes | The number of bytes sent in the egress direction using the IPv6 protocol |
cr_ipv6_ingress_bytes | The number of bytes sent in the ingress direction using the IPv6 protocol |





